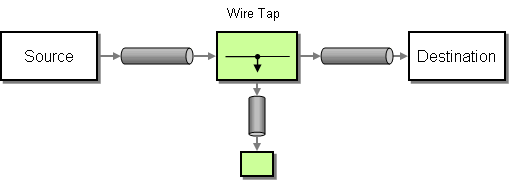
I read in IEEE Spectrum July 2007, a detailed technical analysis of how a high-profile mobile phone bugging that happened in 2004. It was of Greece Prime Minister, his cabinet colleagues in defense and foreign affairs, MPs and others. The interesting thing the authors (Vassilis Prevelakis, Diomidis Spinellis) point out was the fact the whole episode was undetected for several months. The hackers (till date even after a Greece Parliament Commission was not identified) had used very sophisticated techniques to hide traces of their activities and ensured they left no entries in any logs.
The cellphones of Greece PM and others were wiretapped to unauthorized numbers by hacking into Ericsson’s AXE Switches used in Vodafone Greece mobile network and installing RootKit softwares. Ericsson switch software has the ability to patch its Operating System code without rebooting by using something called has Correction Area. The hackers installed about 29 blocks of code in this correction area, tampered all checksums to go undetected, modified (made itself hidden) the list of active processes in memory. The rogue software stored all the mobile numbers that has to be tapped in memory (there by avoiding any disk entries) and copied the voice calls to parallel numbers.

IMAGE: Bryan Christie Design. Courtesy: IEEE Spectrum July 2007
From a software best practice angle, what was interesting was this could have been identified much earlier if Vodafone had purchased a front-end (GUI) software called IMS (Interception Management System) that maintains a list of legal wiretapping numbers. This list could have been compared periodically with what was in memory and any differences between the two alerted immediately. In this case, the backend OS in the switch had legal wiretapping capabilities enabled and working, but the front-end to manage it was not purchased by customer. Clear case of not reducing the attack surface area by removing unwanted piece of software in live environments.


Most popular soft for youtube video.